Overview
The nature, frequency, and severity of cyber attacks continues to grow and evolve. Public sector and local government entities, regardless of size or location, are a target because of what they do and the type of information they hold. Cyber incidents may compromise entities’ information systems and business operations – significantly disrupting the delivery of critical public services. This can have long-lasting economic and social impacts. All entities need to proactively manage their cyber security risks, identify vulnerabilities, and importantly, ensure they can respond to an incident.
Tabled 4 June 2024.
Podcast – Cyber risk: what do we do now?

Report on a page
Cyber incidents are unwanted or unexpected events that could compromise computer and information systems and business operations. They can cause significant disruption and are happening more often, according to the Australian Cyber Security Centre (ACSC). Across Australia, nearly 94,000 cyber crime reports were made to the ACSC in 2022–23 – a 23 per cent increase in one year. Queensland accounted for 30 per cent of these reports, which is disproportionate to its population size, and one in 8 reports nationally related to state or local government entities. Cyber risks are continuing to evolve, and new technologies such as artificial intelligence increase the risk.
In this report we discuss how prepared Queensland public sector entities, including local governments, are to deal with cyber security incidents. We examined 2 lead agencies with responsibility for guiding cyber security, and we audited 3 other entities with varying levels of resources and capability. We have not named them, to avoid publicly identifying any security vulnerabilities.
The current picture
Since we produced Managing cyber security risks (Report 3: 2019–20), the Queensland public sector has invested in building its cyber resilience. The Cyber Security Unit (CSU – Department of Transport and Main Roads) has worked with entities to improve their information security management systems (their policies and procedures for managing sensitive data). The government has made additional investments to provide support, share cyber intelligence, and assist government owned corporations and local governments.
Despite this, public sector entities are not as prepared as they have to be. Just having plans is not enough. They need to test their plans and readiness. They need to identify and address any skills gaps they have for dealing with cyber incidents. Also, some entities do not yet know about the services CSU provides, and CSU does not know which entities most need its help and expertise.
What entities need to do
The entities we audited had plans for managing cyber incidents, but all had room to improve. Their plans were not always well integrated with their risk management strategies, did not incorporate cyber insurance requirements, and were not designed to respond to a wide range of threats. One entity had struggled to integrate its plans due to consistent machinery of government changes (restructures of government functions). Some entities also needed to be clearer on roles and responsibilities and on how to escalate their responses to cyber incidents. Only one entity had tested its incident response plan, and all entities needed to do more to ensure they can effectively communicate in a cyber crisis. Some entities did not have an up-to-date and complete understanding of their critical systems and information assets – an essential starting point for cyber security.
Entities relied heavily on third parties or other government entities when dealing with responses to cyber incidents, and were not always clear on accountability requirements. None had tested how these third parties would perform in a crisis. This means they could not be confident the third parties would be available or have the expertise to deal with a real incident in an effective and timely manner.
What expert and lead agencies need to do
CSU needs to continue working with entities to improve their information security management systems. It also needs to help entities to assess their individual needs, which would assist it in deciding where to focus its support and training. CSU should also start helping entities test their incident response processes. Again, this will benefit CSU, because it will familiarise its external experts with public sector requirements.
The Department of Housing, Local Government, Planning and Public Works needs to ensure councils are aware of the cyber-related skills available through CSU and encourage them to use them.

1. Audit conclusions
The public sector entities we audited were not as prepared as they need to be. All had response and recovery plans in place, but they were not as effective or complete as they need to be to deal with the complications and risks associated with cyber attacks.
Entities’ capability and confidence in managing cyber incidents varied. We found that those who continually plan, rehearse, and test their people, processes, and technology were more likely to respond and recover effectively.
All of those we audited were reliant on parties outside of their entities for technical expertise and action on cyber incidents. None of them had tested these arrangements to ensure they would work, or to confirm that the third-party experts would provide timely responses in a cyber crisis.
Public sector entities cannot delegate responsibility for managing their cyber risks to an external organisation. Those charged with governance (such as executive management, boards, and councillors) must be satisfied that their entity has plans in place that are fit for purpose and have been thoroughly tested. Only one of the 3 entities we examined in detail had tested its plans. When we ran cyber security simulation exercises, it performed the best.
Entities also do not currently have all the capabilities they need to manage cyber incidents. This relates to technical cyber skills and capabilities, as well as supporting tools. They can access frameworks to guide them in understanding and developing capabilities, and the Cyber Security Unit (CSU – located within the Department of Transport and Main Roads) can help in selecting the appropriate framework and in assessing and developing capabilities.
The expertise of CSU is of great potential value to public sector entities, but not all the entities were aware of the breadth of services it offers, including its ‘communities of practice’, which share intelligence and learnings about cyber threats. CSU needs to address this by publishing a strategic plan and by increasing awareness of its services.
CSU has recently provided services to local governments. These entities – particularly the regional, rural, and remote councils – could benefit from accessing these to help protect themselves against cyber threats. This would help them be more aware of the risks they are facing and of the training, guidance, and resources they can access to help them deal with cyber threats.
The Queensland Government has increased its investment in cyber security, and much is now available to help entities protect themselves. Based on this audit, the lead and expert agencies, and the entities, now need to make a concerted effort to assess the threats; prepare their defences; and take full advantage of the expertise, resources, and intelligence at their disposal.

2. Recommendations
We gave specific recommendations to each of the 3 entities we examined in detail. All public sector entities – big or small – are a target for cyber criminals because of what they do and the information they hold. Cyber attacks are continuing to increase, and all entities need to ensure they are prepared to identify and respond to an incident. Accordingly, we provide the following recommendations, drawn from the learnings of this audit, for the benefit of all public sector entities.
We have also created a checklist of key questions (Appendix E) for those charged with the governance of public sector entities to consider when planning how they respond to and recover from cyber security incidents.
We recognise that implementing effective controls for cyber incident response should be performed on a cost-benefit and risk basis. Entities should decide, based on their individual organisational needs, the extent to which they can and should act on each of the following recommendations.
| Chapter 4: The role of public sector entities in managing cyber incidents |
We recommend all public sector entities:
|
|
|
|
|
|
| Chapter 5: The role of expert and lead entities in managing cyber incidents |
We recommend the Department of Transport and Main Roads – Cyber Security Unit:
|
|
|
|
We recommend that all statutory bodies:
|
We recommend that all government owned corporations and local governments:
|
We recommend the Department of Transport and Main Roads – Cyber Security Unit:
|
We recommend the Department of Housing, Local Government, Planning and Public Works:
|
Reference to comments
In accordance with s. 64 of the Auditor-General Act 2009, we provided a copy of this report to relevant entities. In reaching our conclusions, we considered their views and represented them to the extent we deemed relevant and warranted. Any formal responses from the entities are at Appendix A.
Technical language
Cyber security is a complex field, and the language about it reflects this. It is necessary to use some of this language to be precise, but we have explained and simplified it in this report and provided definitions when necessary. We have provided extra details on many of the terms in the glossary (Appendix G).

3. Managing cyber incidents
A cyber incident is an unwanted or unexpected event that is likely to compromise computer and information systems and business operations.
The economic and social impacts of cyber incidents can be significant and long lasting, so entities must be proactive in managing their cyber security risks. The Australian Cyber Security Centre (ACSC – part of the Australian Signals Directorate) states that the most effective way to defend against cyber incidents is to implement appropriate preventative strategies. We covered some of these strategies in Managing cyber security risks (Report 3: 2019–20). If entities adopt them, they can reduce, and in some cases, prevent cyber threats.
The changing nature of technology means that cyber security threats evolve rapidly. This is compounded by the development of new technologies such as artificial intelligence and machine learning. For a measure of how damaging cyber security incidents can be, we only have to look at recent events at organisations such as Medibank and Optus.
Even the best prepared organisations can be susceptible, so all entities need to have effective plans in place to minimise potential damage. They need to be informed about the risks, and ready and able to manage them.
Figure 3A shows the cyber security life cycle focus of our 2 reports. In Managing cyber security risks (Report 3: 2019–20), we mainly concentrated on prevention and preparedness (shown on the left-hand side of Figure 3A). This report examines response and recovery (right-hand side).
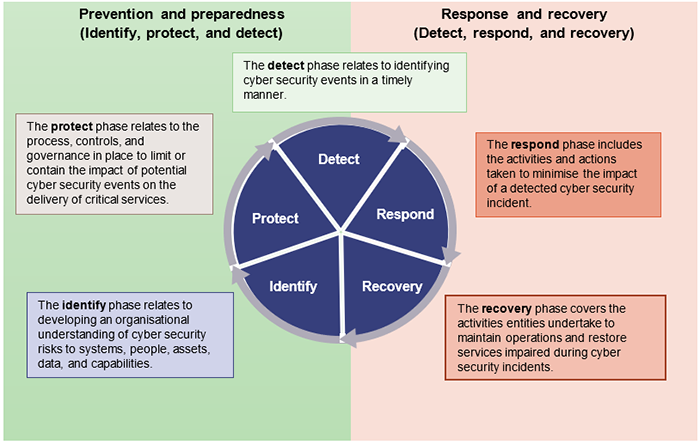
Compiled by the Queensland Audit Office using information from the National Institute of Standards and Technology (NIST) Cyber Security Framework 2.0.
Cyber incidents in Queensland and Australia
The ACSC reported that in 2022–23, cyber incidents, including those impacting government entities, have increased in frequency and severity.

Compiled by the Queensland Audit Office using information from the Annual Cyber Threat Report, July 2022 to June 2023 – Australian Signals Directorate.
Roles, responsibilities, and requirements for responding to and recovering from cyber incidents
Figure 3C shows how roles, accountabilities, and responsibilities for cyber response and recovery activities within Queensland state and local governments are split between expert government agencies and individual entities.
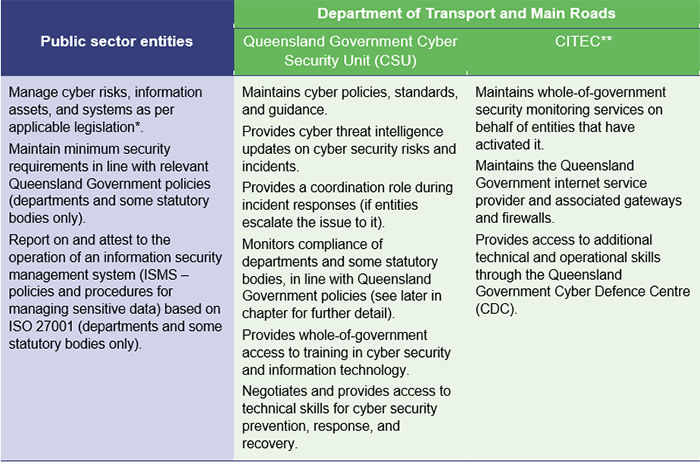
Notes:
* Financial and Performance Management Standard 2019 for departments and statutory bodies, Corporations Act 2001 for government owned corporations, and Local Government Regulation 2012 and City of Brisbane Regulation 2012 for local governments. Public sector entities may have further legislative requirements depending on the nature of their operations. Refer to Appendix D for further information and relevant Acts.
** CITEC is the Queensland Government’s shared corporate service provider for information and communication technology services.
Queensland Audit Office from Queensland Government website.
Better practice frameworks and Queensland guidance
Appendix C lists different international, national, and state frameworks, policies, and guidance, which we refer to collectively as ‘better practice frameworks’.
Entities can access a variety of national and international frameworks to help them in managing cyber risks. Figure 3D shows the overall Queensland Government approach, which includes the overarching Queensland Government Enterprise Architecture (QGEA), the Queensland Government Information Security Policy (IS18:2018), and related standards and frameworks.
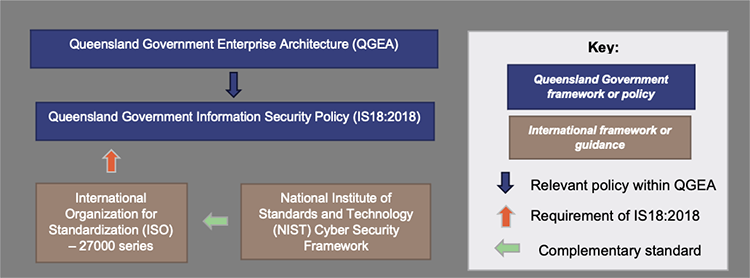
Queensland Audit Office.
The Queensland Government Enterprise Architecture is a collection of publications such as digital and information and communication technology (ICT) strategies, frameworks, policies, and other guidance materials. These publications aim to support the efficient and effective use of digital and ICT resources across government.
The Queensland Government Information Security Policy (IS18:2018) aims to ensure all departments apply a consistent, risk-based approach to information security to maintain confidentiality, integrity, and availability. While IS18:2018 only applies to departments defined under the Public Sector Act 2022, all Queensland public sector entities, including local governments, should consider the policy.
The ISO 27000 series is a set of standards for establishing an information security management system and underlying controls. It includes a library of technical controls and requires entities to conduct training and awareness activities. To be compliant, entities must conduct a risk assessment and design and implement security controls, and regularly review their effectiveness.
The National Institute of Standards and Technology (NIST) Cyber Security Framework is a risk-based approach to managing cyber security risk. It reinforces the relationship between cyber security activities and the business operations of an entity.
All public sector entities are responsible for managing their cyber security risks and being prepared to respond and recover when cyber events occur. However, policy requirements differ between different types of public sector entities, as outlined in Figure 3E.
|
Public sector entity |
Relevant requirements |
|---|---|
|
Departments |
All departments must apply the policy requirements in IS18:2018 to all information, applications, and technology assets. This includes the requirement to comply with ISO 27001. Departments may apply other frameworks in addition to this if they consider them suitable to their needs. |
|
Statutory bodies |
All statutory bodies must have regard to the QGEA, including IS18:2018 and ISO 27001. This means that they must consider and document whether the framework applies to their circumstances in setting their own internal controls and policies. Statutory bodies may also adopt other frameworks they consider suitable for their needs. Some statutory bodies may be directed to comply with IS18:2018 by their minister or chief executive. |
|
Government owned corporations |
Government owned corporations (GOCs) do not have to comply with QGEA or IS18:2018 requirements. However, in accordance with the Corporations Act 2001, GOC boards are responsible for ensuring appropriate controls and processes are in place to address identified risks (which includes cyber-related risks). |
|
Local governments |
Local government entities do not have to comply with QGEA or IS18:2018 requirements. However, in accordance with risk management requirements in their regulations, they are required to develop and implement fit-for-purpose strategies to address identified risks (which includes cyber-related risks). |
Queensland Audit Office.
Other legislative requirements
Public sector entities may have additional legislative obligations relating to cyber incidents. These obligations are dependent on the nature of their business and operations. For example, many public sector entities will hold personal information and may have reporting obligations under relevant privacy legislation, while those entities who own or operate critical infrastructure (services that are essential for everyday life, such as energy, communications, water, transport, and health) will have additional obligations under the Security of Critical Infrastructure Act 2018 (Commonwealth). We provide further detail on these obligations in Appendix D.
What we audited
In this audit, we assessed the role of lead agencies, and the preparedness of 3 public sector entities to respond to and recover from cyber security incidents. The entities have different levels of resourcing and capability for managing cyber security risks. We do not want to compromise the security of these entities by publicly identifying their security vulnerabilities, so we have not named them in this report.
Appendix B provides greater detail on our audit scope and methodology.
We use the term ‘entities’ in this report to refer broadly to all Queensland public sector entities (departments, statutory bodies, and government owned corporations) and local governments.

4. The role of public sector entities in managing cyber incidents
In this chapter, we report on how prepared the 3 entities we audited were in relation to responding to and recovering from cyber incidents. They may not be representative of all public sector entities in Queensland, and results cannot be extrapolated. However, all public sector entities should consider our findings and recommendations to determine if they are relevant to their own organisations and risks.
We identified a range of gaps and improvement opportunities in the audited entities’ approaches to cyber response and recovery. Figure 4A summarises the gaps across the areas we audited, which were:
- risk assessment
- incident response plans
- capability and sharing cyber threat intelligence (and lessons learnt).
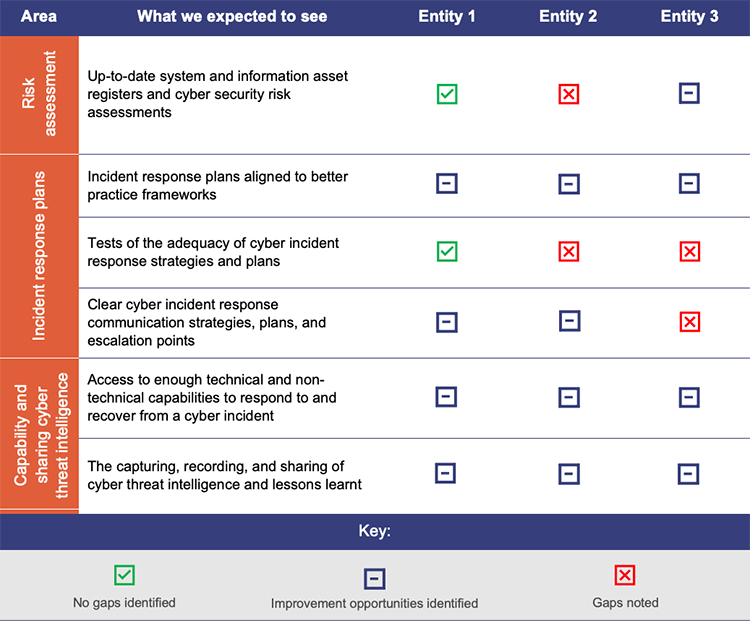
Queensland Audit Office.
Understanding cyber risks in system and information assets
Public sector entities must understand the systems they have and the information assets contained within them. This is essential if they are to effectively identify all potential risks that may be exploited by threat actors. They should periodically undertake cyber security risk assessments of key systems and those information assets that increase risk because of the desirability of the data they contain. These assessments should consider all possible points of system access by threat actors.
Of the 3 public sector entities we audited, 2 did not have an up-to-date or complete listing of the systems and information assets they held, and their risk assessment activities were not up to date. These entities did not have the information they needed to identify key risks and assess the potential business impacts on their operations.
A threat actor (also commonly referred to as a cyber criminal) is any person or organisation that intentionally exploits weaknesses in computers, networks, and systems for gain or to disrupt individuals or services.
Managing cyber risks from third-party systems
Not all entities manage their risks themselves. Some have contracts with other organisations to provide access to the necessary expertise and resources, including systems. In this report, we refer to these as ‘third parties’.
Not all the entities we examined had considered risks for critical systems and information assets managed by third parties. This means they were unaware of potential risks, and were therefore not actively managing these risks.
It is important for all public sector entities to consider cyber security risks relating to third-party arrangements. They should ideally do this prior to setting up or extending contracts. In this way, they can ensure appropriate arrangements (such as the provision of assurance certificates, which outline effectiveness of system controls and processes) are in place through contractual obligations.
We plan to conduct an audit on managing third-party cyber security risks in 2025–26.
Impact of machinery of government changes on cyber risks
Machinery of government changes (restructures of government functions) can cause disruption to public sector entities.
One of the entities we audited had been through various machinery of government changes over the last 5 years. As a result, it was using and relying on several systems managed by other government entities. This adds to the complexity of managing and responding to risks of a cyber incident. The entity did not have a well-integrated incident response plan and recovery plans to guide it in the event of a cyber incident.
It is important for any entity impacted by a machinery of government change to identify and understand its new critical systems in a timely manner, so it can manage its risks. Entities also need to clarify the roles and responsibilities for managing cyber incident responses across the new structure.
We have previously produced a guide – Checklist for managing machinery of government (MoG) changes – to assist entities to identify, manage, and monitor the associated operational and strategic risks.
|
Recommendation 1 We recommend all public sector entities protect their systems and sensitive information by:
|
Improving incident response plans
An incident response plan (IRP) is critical to incident response and recovery. It supports a swift and effective response to cyber incidents, in line with an entity’s security and risk management strategies and plans.
Alignment to better practice
All entities we examined had an IRP. Figure 4B provides a summary of the strengths and weaknesses we found when comparing these plans to better practice frameworks.
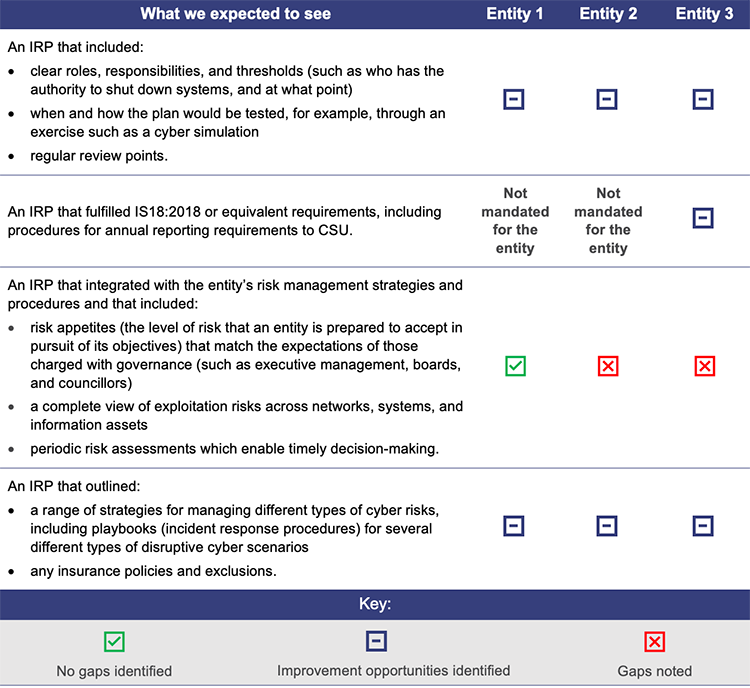
Queensland Audit Office.
All public sector entities should continually improve their IRPs, particularly the playbooks they produce for managing different types of cyber risks.
Being fully compliant with better practice frameworks can require significant investment. Accordingly, entities have to decide and document the extent to which they are prepared and can afford to align to better practice frameworks, in line with their resources and risk appetites.
Entities told us that they would benefit from more guidance on how to effectively respond to common cyber risks and incident types. Common incident types include:
- ransomware (demanding payment to let entities into their own files)
- insider privilege abuse (by current or former employees with access to the system)
- social engineering (manipulating employees into giving up information)
- denial of service attacks (flooding a network to disrupt operations)
- malware (gaining access to a system via software)
- phishing (enticing users to share confidential information).
Appendix G provides more details on each of these incident types.
| Better practice approaches |
An effective incident response plan:
An effective IRP must be a ‘living document’, meaning it is continually rehearsed, tested, improved, and supported with training and a culture that promotes cyber resilience. |
Understanding insurance arrangements
Having effective strategies and plans does not eliminate the risk of a cyber incident. Entities need to consider how they manage that residual risk. Many use cyber insurance arrangements to do this, as this can be an effective way to protect entities from financial impacts and losses. Those entities who do this need to fully understand their coverage and requirements and integrate them into their incident response planning.
Some of the entities we audited did not fully understand specific clauses and escalation points in their insurance arrangements. This could have meant that their insurance coverage was at risk in the event of a cyber incident.
Accountability for cyber risks
Some of the entities we audited had not clearly defined incident response roles, responsibilities, and accountabilities. One entity had assigned, through a memorandum of understanding, most information and communication technology (ICT) accountabilities to CITEC (a Queensland Government shared corporate service provider for ICT), including most cyber security monitoring and response.
Ultimately, the responsibility for cyber risks (as with all risks) rests solely with the accountable officer and they cannot assign it to external entities, including other government bodies. The accountable officer must be satisfied that third-party arrangements adequately reduce risks to an acceptable level. We discuss testing of third-party arrangements later in this chapter.
Testing cyber incident response strategies and plans
As entities are ultimately responsible for their own systems and information assets, they should regularly test their IRP and business continuity plans (plans which entities use to ensure they can continue to operate in the face of major business disruptions) to make sure they can adapt to the ever-evolving threat of cyber attacks. Those entities who regularly test their processes, people, and technology for a variety of cyber security incidents should have an increased chance of success.
Only one of the 3 entities we audited had previously tested its IRP through an entity-level cyber security simulation (one it conducted itself, of its own processes) to ensure that it was fit for purpose. This entity performed the best in our simulations.
Cyber security simulations are workshops to test how key incident response personnel (both technical and non-technical) respond to a cyber incident within their information systems or networks. Simulations can help identify vulnerabilities, assess risks, and improve security measures.
Testing third-party arrangements through simulations
All 3 entities were reliant on third-party capabilities as a part of their incident response plans, but none had ever tested these arrangements.
It is important to use simulations to test any third-party arrangements. They give entities insights into whether they will deliver the services and expertise needed in the event of an actual incident. Public sector entities should not be testing these arrangements for the first time during an incident.
For third parties to be effective and respond promptly to incidents, they need to become familiar with public sector systems and environments. The greater the reliance entities place on these arrangements, the more time and effort they need to invest in familiarising the third parties.
| Lessons from our cyber simulations |
All audited entities participated in our cyber simulations. These identified valuable lessons and opportunities to improve for each of the entities. Some examples we noted were:
|
The following case study shows the importance of a quick response in the event of a cyber incident.
Maersk NotPetya cyber incident | ||||||||
|---|---|---|---|---|---|---|---|---|
The Maersk NotPetya cyber incident, which occurred in June 2017, escalated rapidly, causing widespread disruptions and significant damage to Maersk, one of the world’s largest shipping companies. The following timeline highlights the key events and escalation of the incident:
|
Queensland Audit Office, compiled from various news articles, podcasts, and journals.
Whole-of-government cyber security simulations
The CSU has conducted annual whole-of-government incident response simulations for the past 3 years. These simulations have had good participation rates from Queensland Government departments.
The main objective of these simulations has been to test the Queensland Government Cyber Security Operations Plan. The plan aims to detail the whole-of-government coordination and communication response to cyber incidents.
These simulations are important and should continue to be held at regular intervals. They test different events and scenarios to continue building resilience at a whole-of-government level. However, the simulations have not been designed to assess the preparedness of individual entities to respond to or recover from a cyber security incident.
During our audit, one entity was under the misconception that its participation in CSU’s whole-of-government simulations was evidence that its incident response plans and approach were effective. CSU should take steps to fully educate entities participating in its whole-of-government simulations on the limitations of what these simulations mean for them. We discuss this further in Chapter 5.
Recommendation 2 We recommend all public sector entities formally recognise in key governance documents that responsibility for cyber security rests with the chief executive, or equivalent. Recommendation 3 We recommend all public sector entities improve and test incident response plans by:
|
Planning communication strategies and escalation points
In a time of crisis, trust erodes when the public, employees, and customers are not provided with timely, consistent, or informative communication. In accordance with better practice frameworks, we expected entities to have clear, consistent, and endorsed communication plans, protocols, and templates to guide their communication in the event of a crisis. Not all did.
For those that did have communication plans and templates, most of the documents were in draft and incomplete. The cyber crisis communication plans were commonly missing clear processes and thresholds for:
- contacting those charged with governance, relevant ministers, the Department of the Premier and Cabinet, and CSU
- contacting key stakeholders (such as employees, insurers, Office of the Information Commissioner, and the public)
- escalating communication to other agencies.
Entities showed a lack of consistent content and messaging in internal and external communications during the cyber security simulations. This inconsistency could result in a lack of trust if internal messaging is found to be inconsistent with external messaging.
Recommendation 4 We recommend all public sector entities improve their crisis communication plans and templates by:
|
Capabilities for incident response and recovery
Entities may require access to a broad range of skills, capabilities, and tools to effectively navigate a cyber incident. These span:
- technical areas such as digital forensics (the ability to assess the source and extent of a breach) and a security operations centre (which is the focal point for network security operations)
- non-technical areas (such as crisis management and communication)
- general ICT areas (such as system applications and networks).
We refer to these collectively as ‘capabilities’ within this report. These may be sourced through a combination of in-house and third-party resources.
While all 3 chief information officers (or equivalent) were aware of limitations in their own entities’ cyber technical skills, none of the entities had formally assessed their capability. They need to do so, in detail, to ensure they understand and can address any gaps.
Public sector entities can consider several models in formalising a skills and capability assessment. In Appendix F, we provide an example framework that details the key technical and non-technical capabilities required for cyber incident response and recovery. It can be used by entities to assess their capabilities.
We discuss broader capability building across Queensland public sector entities further in Chapter 5. Appendix G – Glossary, provides more detailed explanation of the various capabilities needed to manage a cyber incident.
Recommendation 5 We recommend all public sector entities gain access to the technical skills required to respond to and recover from cyber incidents by:
|
Capturing, recording, and sharing cyber threat intelligence
All audited entities demonstrated an understanding of the importance of sharing cyber threat intelligence (CTI). However, for each entity, weaknesses were identified in the processes put in place to capture and share learnings. Gaps were identified in relation to:
- processes on where and how to capture lessons learned, and how to conduct assessments of incidents
- the tracking and monitoring of actions and/or recommendations arising from lessons learned exercises
- identification of external stakeholders to share information with, and the correct medium for sharing.
This could lead to a missed opportunity for the sector to build cyber resilience.
Cyber threat intelligence is information that helps entities better protect against cyber incidents by increasing their understanding of current and emerging threats and vulnerabilities. It can incorporate recent threat actor behaviours and successful remedial procedures, tools, and techniques.
|
Better practice approaches |
|
All public sector entities can strengthen their cyber resilience by:
CTI can come from a variety of sources. The Australian Cyber Security Centre and CSU both produce CTI reports and alerts for their subscribers. These contain critical information about vulnerabilities and how to prevent, contain, and strengthen controls. The most effective collection of CTI is through reporting of actual incidents that occur at individual entities. Many entities use the same products, networks, hardware, systems, and applications. As such, it is likely that if one entity has a vulnerability, another will also have the same entry point. Better practice frameworks recognise the potential for reoccurrences of an incident as an opportunity to learn. |
|
Recommendation 6 We recommend all public sector entities share cyber threat intelligence and lessons learnt with CSU and other public sector entities as quickly as possible. |

5. The role of expert and lead entities in managing cyber incidents
In this chapter, we report on the effectiveness of lead and expert agency strategies for supporting state and local government entities in managing cyber incidents.
The role of the Queensland Government Cyber Security Unit
The Queensland Government Cyber Security Unit (CSU), within the Department of Transport and Main Roads, is the lead agency for Queensland cyber security operations and management.
CSU sets cyber security policy and guidance for Queensland Government departments and statutory bodies, providing:
- cyber security leadership
- governance, policy, and standards
- coordinated responses to cyber security incidents
- development of cyber security capability across government
- greater cyber security awareness.
CSU also provides assistance to local governments and government owned corporations.
Promotion and awareness of CSU’s products and services
CSU plays a critical role in supporting public sector entities across Queensland in the management of cyber security. In June 2023, the Queensland Government committed $73.5 million in additional funding to CSU over 4 years (from 2023–24 to 2026–27) and $17.8 million ongoing (from 2027–28). This was to expand and improve the services CSU provides.
CSU needs to do more to increase awareness of its services and increase its engagement with entities. Its services, such as access to specialist skillsets to assist entities during a cyber incident, can assist in the management of risks and in building capabilities within entities. However, it currently provides limited documentation outlining what products and services are available and the benefits of using them.
It has put initiatives in place, such as communities of practice, to help build awareness, but more is needed to capitalise on the investment the Queensland Government has made. Not all entities we audited had awareness of CSU’s products and services specific to managing and coordinating cyber security response and recovery.
CSU’s communities of practice aim to raise awareness of information security and develop and share information, methods, and tools to create a knowledge base for public sector entities. They also provide opportunities to meet other practitioners and share cyber threat intelligence across the government. Membership of the communities of practice is voluntary and is open to all state government and local government employees.
Publishing a strategic plan
While CSU has a vision, it does not have a strategic plan. It also does not have supporting plans in place to implement its vision – which is important to address areas such as key person risk. We would expect to see a strategic plan that covers, at a minimum:
- the vision, purpose, mission statement, and role of CSU in managing cyber risks across the state
- strategic objectives that will drive the vision
- current challenges and services of CSU
- key threats in the current Queensland environment
- key performance indicators or performance targets to measure effectiveness.
CSU has drafted the Queensland Government Cyber Security Operations Plan, which has been circulated for consultation. The objective of the plan is to facilitate coordinated and cooperative escalation and response during a cyber incident.
It is designed to acquit CSU’s responsibilities for responding to a whole-of-government cyber incident under the disaster management arrangements. It does not cover CSU’s broader role, responsibilities, or services.
The New South Wales and Victorian governments’ equivalent cyber security units have published their strategies and plans across their jurisdictions.
Leading the public sector in increasing cyber resilience
Guidance materials to better support entities
CSU provides public sector entities with access to a variety of guidance and materials to support the management of cyber risk. In September 2018, it issued the Incident Management Guideline. The guideline provides information for Queensland Government departments on the recommended practices for establishing and implementing an information security incident management policy and a planned, systematic approach to handling an incident.
It appropriately references the relevant framework, ISO 27000 incident management standard (ISO 27035). It also provides entities with an example playbook (incident response procedures) on phishing (tricking entities and individuals into providing access to data and information, often through fraudulent emails or texts).
On its website, CSU also provides links to more guidance including:
- Australian Cyber Security Centre resources
- other ISO standards
- both the Australian and Queensland Information Commissioner websites, given their roles in information management
- various other legislation, policies, and guidance, and other resources.
CSU’s guideline could be enhanced by:
- including updates for the most recent release of the ISO 27035 (2023)
- developing and sharing practical examples for a range of common cyber scenarios.
All 3 of the entities we audited stated that they would appreciate more guidance from CSU on how to improve their incident response plans and promote a culture of continuous improvement, to help them stay across the rapidly changing cyber risks facing the public sector.
|
Recommendation 7 We recommend that the Department of Transport and Main Roads – Cyber Security Unit improves awareness of its products and services and enhances its guidance for developing incident response plans by:
|
Helping public sector entities test their incident response plans
As detailed in Chapter 4, CSU conducts cyber simulations that test the response to cyber incidents at the whole-of-government level. While this is an important exercise, public sector entities must also regularly test their individual readiness to respond to a cyber incident. To date, CSU has not assisted entities in coordinating or running individual simulations.
The investment made in CSU to provide public sector entities with access to incident response capabilities has been an important step. This work is undertaken through CSU by a panel of third-party incident response providers. It is expected that many public sector entities will use CSU’s incident response capabilities, but these capabilities must be tested within entities’ environments.
For CSU to be fully effective and able to deliver timely incident response services, its external providers must understand the systems and environments they are working with. Being involved in cyber simulations at individual entities presents CSU with an opportunity to assist the entities with their own readiness, and to ensure that its incident response providers build the necessary understanding of public sector entities.
|
Recommendation 8 We recommend the Department of Transport and Main Roads – Cyber Security Unit assists public sector entities in conducting cyber simulations by:
|
Understanding the current state of public sector cyber capability
CSU is responsible for supporting the development of the Queensland Government’s cyber security workforce. As with many professions, experienced and qualified cyber security consultants are in high demand.
At present, CSU does not fully understand the level of capability within public sector entities. It has not assessed entity-level capabilities or (as previously discussed) provided support to public sector entities in assessing them. Doing so would enable it to better target its investment in building cyber resilience by directing resources and training to the most significant gaps.
Numerous frameworks are available to assist in identifying and developing cyber skills and capabilities. One such example is the Australian Signals Directorate (ASD) Cyber Skills Framework. The skills framework (Figure 5A) helps users map and develop skills using 9 cyber role definitions, 9 capability and skill definitions, 7 proficiency levels, 4 career pathways, and a learning and development pathway.
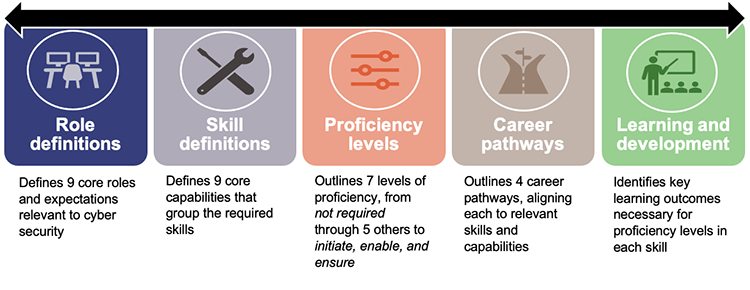
Queensland Audit Office from Australian Signals Directorate’s Cyber Skills Framework.
Providing cyber security and technology training
CSU provides training courses ranging from basic computer operations to full cyber security certificates. These courses are offered to public sector employees at cost, or subsidised depending on the course and the type of public sector entity. They are not targeted to specific roles or agencies.
Figure 5B shows an increase in training uptake since 2020, when the training opportunities were reduced during COVID-19. CSU has engaged external providers to offer a variety of courses in the last 5 years (January 2019 to December 2023). This has increased from 2 courses in 2019, to 22 courses in 2023, with a total of 867 participants completing courses over this period.
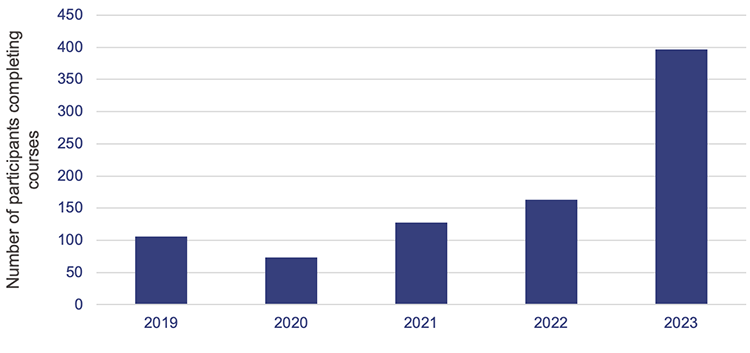
Queensland Audit Office from Department of Transport and Main Roads – Cyber Security Unit data.
While the delivery of training has increased, CSU’s current training offerings may not be meeting the needs of the Queensland public sector. CSU performs limited analysis on training data. It is not aware of whether the courses are being undertaken by the public sector entities and employees who have capability gaps. It needs to examine its funded courses – by entities, attendees’ positions, and whether they completed all the content – to build this understanding.
CSU also needs to be more targeted in its training offerings. It could better align them to the needs of entities and their staffs’ development needs to ensure that significant capability gaps are addressed. CSU’s lack of understanding of current capability gaps across the sector has prevented it from doing this.
|
Recommendation 9 We recommend the Department of Transport and Main Roads – Cyber Security Unit increases public sector cyber skills and capabilities through:
|
Improving information security management systems
Chief executives of departments and some statutory bodies (those who have been directed to comply with IS18:2018 and its annual return requirements, refer to Chapter 3) must attest to the appropriateness of their information security under IS18:2018 (the Queensland Government’s information security policy). This includes providing an information security annual return by 30 September each year. A third party must conduct periodic reviews of the annual returns to assess the entity’s information security management system (ISMS) to conclude:
- if it is fully operational
- if it aligns with ISO 27001
- its overall effectiveness.
Entities must publish the results in their annual report.
CSU consolidates returns and reports outcomes to chief executives. Since our last audit on cyber security in 2019–20, CSU has assisted in-scope entities to improve their ISMSs, increasing overall compliance with IS18:2018 (Figure 5C). In 2019–20, only 18 per cent of departments had appropriately designed and implemented an ISMS. By 2022–23, 86 per cent had one.
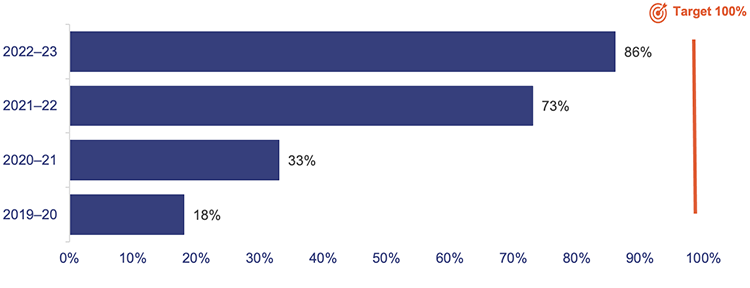
Queensland Audit Office from Department of Transport and Main Roads – Cyber Security Unit ISMS report.
ISMS compliance reviews are only required for departments and some statutory bodies that fall under IS18:2018 requirements. Other public sector entities are not required to review their ISMS, but are encouraged to do so. This restricts CSU’s ability to monitor risks and capabilities at the entity level, outside of departments and those statutory bodies who comply. The policy states that all statutory bodies must have regard to IS18:2018. This means that they must consider and document whether the framework applies to their circumstances in setting their own internal controls and policies. It is unclear whether all statutory bodies have undertaken and documented this assessment. One of the entities we audited had considered this and adopted the principles of IS18:2018, but this was not documented or shared with CSU. For government owned corporations and local governments, there is no requirement to do this.
Also, current IS18:2018 requirements do not explicitly address incident management readiness, which can only be tested through cyber security simulations. Testing of incident management plans is critical to improving the effectiveness of cyber responses.
|
Recommendation 10 We recommend the Department of Transport and Main Roads – Cyber Security Unit improves the maturity of information security management systems by:
|
|
Recommendation 11 We recommend that all statutory bodies document their assessment as to whether IS18:2018 is applicable to their circumstances, and report this information to CSU. If applicable, statutory bodies should apply and adopt IS18 requirements. Recommendation 12 We recommend that all government owned corporations and local governments document whether IS18:2018 is appropriate for their environments, and if not, which frameworks are being applied to manage information security risks. |
Increasing cyber threat intelligence and transferring knowledge
CSU runs communities of practice with technical and security leads from across the Queensland public sector. These forums are used to share cyber threat intelligence, provide updates, advocate for learning or training opportunities, and share ideas.
The following case study demonstrates the value of acting promptly on shared intelligence.
| Cyber Security Unit amber alert |
|---|
|
In December 2021, following a public sector entity reporting a phishing incident, CSU provided an amber alert to entities. Within 2 hours, one of the entities we audited was able to alert its employees of the potential phishing and begin reviewing its system applications. Within a day, it had removed the vulnerabilities from its environment and contacted all its service providers to patch the vulnerabilities. |
Queensland Audit Office from departmental records.
This case study shows the value in CSU promptly sharing cyber threat intelligence through alerts to entities. However, 2 of the 3 entities we audited were not aware of the community of practice forums. CSU needs to improve awareness of its activities.
All 3 entities had ideas for additional guidance and better practice frameworks for CSU to share through its communities of practice. A key example was generic playbooks for various cyber scenarios – for entities to customise to their needs and circumstances.
|
Recommendation 13 We recommend the Department of Transport and Main Roads – Cyber Security Unit shares cyber threat intelligence and lessons learnt by:
|
Increasing cyber resilience in the local government sector
Local governments deliver a range of critical services to the public, such as water and sewerage services. They must be as prepared as possible to manage a cyber incident. The following case study demonstrates the prolonged and costly consequences cyber incidents can have on local governments if they are not able to access the required cyber incident response skills in a timely manner. It includes 3 examples which impacted councils since 2020. These councils included regional councils, and those with both small and large populations.
| Impact of cyber attacks on councils |
|---|
|
Example 1 In 2023, a Queensland council became a victim of a cyber attack that used ransomware (where a threat actor locks electronic files through encryption and demands a payment to unlock them). The incident occurred on a Saturday morning before systems were switched off over the weekend. The council had to access cyber security expertise from a third party who was flown in 2 days after the initial event. Twelve days into the incident, the council identified, with the help of third-party digital forensics skills, the potential entry points for the ransomware. The likely scenario was through a phishing email and a council worker clicking a malicious link. Council did not pay a ransom to access its locked data. The continued disruption meant the postponement of an important oversight committee – council’s April 2023 Standing Committee meeting. It also meant phone connections could not be restored until May 2023. |
|
Example 2 In 2022, a Queensland council was subject to a ransomware attack on a network responsible for operating public infrastructure. The impact to the business was significant and included access to assets, systems, and services which were used by the council, external government bodies, and the public. The time between the initial identification of the incident to recovery attempts took approximately 2 days before the decision was made to shut down the network containing those services. The recovery process from this attack took a further 24 days, with permanent corrective actions taking a further 12 months to complete. This incident was reported to the Australian Cyber Security Centre (ACSC) and the Queensland Government CSU. |
|
Example 3 In 2020, one regional council was subject to a ransomware attack. The cyber attacker gained access to all council systems, including the backup data that was stored on the council’s network. The impacts of this attack were that:
This incident was reported to the CSU. |
Queensland Audit Office.
Local governments do not have to comply with or have regard to Queensland Government policies and requirements, including IS18:2018. They can choose a cyber security incident response framework that best suits them.
There are no central strategies, policies, or procedures for managing and coordinating cyber response and recovery capabilities specific to local governments. However, CSU has been funded to provide them with essential cyber advice and services. Given the large variability in capabilities and resources available across the local government sector, this presents both a challenge and an opportunity.
One of the entities we examined in detail in this audit was a local government, which was not aware of the CSU’s support offerings prior to the audit but has since started engaging more frequently with it.
The role of the Department of Housing, Local Government, Planning and Public Works and the councils themselves
As the lead department for local governments, the Department of Housing, Local Government, Planning and Public Works (the department), has a role in providing advice to councils on managing risks – to ensure they comply with the requirements of the Local Government Act 2009 (or equivalent) and associated regulations. These include cyber security risks, but the department does not have the requisite skills to provide specialist advice to councils regarding cyber response and recovery. It can do more to raise awareness and connect the councils with CSU.
Local governments could also consider establishing agreements with neighbouring councils to increase their access to expertise in the event of a cyber-related crisis. This can be a cost-effective solution for smaller, regional, or remote councils that cannot afford to have in-house cyber security expertise or access it externally.
Recommendation 14 We recommend the Department of Housing, Local Government, Planning and Public Works increases local governments’ knowledge of available support by partnering with CSU to:
|
